There is a whole category of threats to cyber risk and security often ignored despite its potential to impose catastrophic disruption and damage—business interruption! We attend to human malice in many forms, and its diverse efforts to gain unauthorized access to secure information, capture control of devices and systems, or perform all kinds of mischief and malevolence. All too often we ignore the greatest source of disruption to our daily lives, our achievements and constructions, business and personal—the earth and the weather that envelops everything within it.
Business continuity planning is often met with yawns accompanied by apprehensions over extensive, boring, even pointless detail. “We haven’t had an earthquake in 120 years!” “It never rains heavily here!”. “Why are we wasting valuable resources to plan for something that may never happen?” I’ve heard these remarks and many others like them over and again. Then something that’s “never happened before” occurs. And the fingers begin to point accompanied by voices raised in frustration and a bit of fear, neither of which helps advance anything towards a more positive state.
Velocity is Key
Often when we assess risk we think about some formulaic product of likelihood and impact. This leads us, sometimes, to dismiss high impact events of very low probability as virtually risk free situations. At least, they are so low on the risk score scale they receive very minimal attention, planning, or consideration of any kind. We ignore another variable that completely changes the analysis—velocity! Simply, velocity is an estimate of how quickly an event, once it starts, will reach maximum impact. Pandemics take a while to get there, but persist. Hurricanes, earthquakes, terrorist attacks, and tornadoes, to name a few, can achieve maximum impact in little time. These events, if they happen, offer little room for thoughtful reaction and response. Only implementing actions planned for and prepared in advance have a chance of any meaningful offset to the disruption and damage inflicted. Your risk scoring and assessment should consider velocity in their processes. As a suggestion consider modifying the simple standard
![]()
To one incorporating velocity
![]()
If you are using numeric scales to assign likelihood and impact, simply extend that practice to velocity too. For those who prefer visual representations of data, one can consider the traditional 2 dimensional heatmap to be transformed into a 3 dimensional one that might look like this:
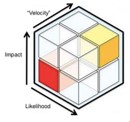
Doing so will help place a more accurate determination of the risk posed by some low frequency but very high impact events that may result in significant disruption to normalcy.
Continuity, Recovery, It’s All In The Planning
Business continuity planning came to the forefront early in the COVID pandemic. While some businesses’ operating models already encouraged remote working, and the infrastructure was in place, for many others it was an uphill sprint to figure out how they could operate and then set up the means to do so. After-the-event planning and execution is always more expensive. And it’s hard to measure lost opportunity and business. But the costs are real. When the interruption results from a disaster, such as may be inflicted by extreme weather events, it’s even more complicated.
Disaster recovery is different than continuity planning. In a disaster you have likely lost key physical resources, infrastructure, and possibly even data on top of the potential loss of services from key staff and leadership. So, in addition to replacing the means to work, or switching to alternative operating practices, suppliers, etc., you may also be dealing with succession chains for key personnel, skills, knowledge and expertise. And you may be doing this in an unfamiliar environment absent of basic services that may be unreliable and unsafe for indeterminant periods.
The point being that while such planning is complex in nature, wide in scope, and best done thoughtfully before there’s a need to put it into action, your risk management process has a significant gap if left undone. It’s also important to note this is not just about writing a plan, putting it in a binder on a shelf, and dusting it off annually for a tabletop review to then re-shelve. It touches almost everything you do, and certainly can be a component of many basic aspects of your risk planning and operation. As already noted, it can touch your staffing, location, technology infrastructure, supplier and partner choices, and more.
Here’s a short list of questions (security and risk related, of course) that should be addressed in your planning. This is by no means complete, but a useful sampling:
- Are your facilities (and perimeters if enclosed), secure if the power fails?
- What communications tools used to reach staff, their families, and critical services will survive an event?
- When was the last time you successfully tested a backup by trying to restore a device from it?
- Are your systems and data safe from a sudden local loss of connectivity and/or power? For how long? How do you know?
- Do you have a succession plan in place with designated alternates for each key position and skill?
- Do you know what roles are key, what skills or knowledge is key, and who has them? Do you know where they are?
- Do you have alternate sources for goods and services provided by your trusted third parties? Do you know and examine their own preparedness as part of your third party risk management (TPRM) process? (hint: if they exchange data with you, or have access to your infrastructure, this is critical to your risk management planning.)
- How does your management of operational infrastructure; data, software, processes, and hardware determine when to engage continuity practices, who and how to initiate disaster recovery, and what authority is assigned to whom for what?
- What cyber specific practices are in place to protect possibly exposed or weakened assets during recovery?
As you can see, the scope of content ranges far and wide throughout your organization. It requires a thorough understanding of what and who are important, essential, and require strategy and planning to assure they remain or regain presence in your company when events require them. Examining your business, making these determinations, crafting and implementing plans to address each aspect is not an overnight task. Even once created and implemented, the plans and processes require periodic testing where feasible, and review to assure they remain valid and current.
Resilient Security In A Remote Operating Environment
Having a workforce that is a mix of onsite and remote presence is a challenge and an opportunity. Significant weather, malicious, or geographic events may be centered in a specific location limiting their impact. Or, they may target a critical piece of infrastructure impacting the ability of staff to access remote data or processes. From a cyber risk perspective, there’s a lot to consider. For example, how resilient are your monitoring tools and perimeter defenses? Would they still be functioning in the event of a significant disaster? If not do they dynamically transfer control to some cloud-based service hosted in a geographically different, and therefore unaffected locale? If not, how would you regain control of your perimeter defenses? And monitoring? And any tool you use to analyze their discovery and take corrective action? Would you be completely vulnerable to cyber attack in addition to whatever event lead to your weakened security?
Your remote workforce likely has whatever security controls and services you offer largely localized to the devices they use. But some might be lost or left behind in an emergency evacuation. Can you remotely disable them? Are they even registered with you so that if you had tools to do so you could try? Are any portable data storage devices all encrypted? Are staff well informed of what to do in case of emergency, so they can react without thought, having planned for an event when their first concern is going to be the safely of family and self, not your hardware or data assets?
Cloud based services offer solutions to address some if not many of these needs. By off-loading the host source of cyber security tools and services you can establish a level of resilience and rapid recovery from significant, even disastrous events. Cloud services, often by intent and design, offer services across geographically disperse locations to sustain service continuity in the event of any incident or happening at a specific site; AWS’s “availability zones” are an example of this concept. Other cloud services offer similar location diversity. Such cloud based services could be used to keep those perimeter monitors and other security protections in place even in the face of a local disaster. They could also host some of the tools remote workers might employ to keep assets safe throughout any evacuations or relocations.
And Then There’s Your Third Parties
As part of your planning don’t forget to examine the readiness of you most important third parties. First, you need to determine which ones are critical to your own business. But that should be a component in the early vetting of prospective candidates in your third party risk management (TPRM) process. In evaluating their own security preparedness, include a review and understanding of the provisions and planning they have to sustain service to you in the event of disruptions. Asking questions about whether they have a business continuity or disaster recovery plan is not enough. Ask about the frequency of testing for key components. How do they protect your data if they have access to it? Do they have backup power, and if so, how often has it been tested? See if they have any related findings from their own SOC reviews or other assessments of their controls and capabilities. Remember, tabletop reviews of plans, by themselves, are not adequate preparations for such events—they are a foundation, but not a fully implemented or operation-ready feature. Third Party business continuity, and disaster recovery efforts are as important to you as their availability to deliver. If they are vital, but not sustainable, be sure you have a quality alternate identified that can step in for the duration of any disruption. Review and reconfirm that alternate’s willingness and capability at least annually.
Leveraging Your GRC
As you may suspect, reviewing these plans and controls, internal and external, is well supported by a comprehensive GRC platform. If it’s one that may incorporate TPRM then the vetting and evaluating of third party suppliers and partners can directly feed into your overall risk assessments and cyber risk evaluations, including planning for the coming year. This kind of data sharing across modules within a GRC is one of the data leveraging powers that these platforms offer. They reduce the time needed to incorporate input from related processes, eliminate duplicate efforts and redundant data collection and entry. As a result, findings and recommendations are based upon consistency and completeness greater than a series of individual efforts may deliver on their own. They help assure context as well as content, and foster a trustworthy foundation for executive actions.
So, When It Rains…
The rains and floods and other incidents may come now, and perhaps even increase their frequency in years to come. But reasonable planning and care for the kind and placement of resources, plus establishment of methods to monitor the effectiveness of your actions, can prepare you to weather those storms and incidents, avoiding your company’s listing with other unfortunate casualties of catastrophe or malice at any level. As always, your choices and actions are the determinants of your future. Manage your risk wisely.
About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through the creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.

