This is the second of a Two-Part blog series on Cybersecurity’s impact on Audit Management, by guest blogger Simon Goldstein.
Cyber Incident Investigation
Partner with Audit to facilitate and enrich Incident Management. When a cyber incident occurs, the immediate need to bring the event to a halt is paramount. At the same time, detailed investigation into the specific facts leading to the incident are critical to determining root cause, significantly impacting determination of effective remediation, and implementation of actions designed to reduce vulnerability to a repeat occurrence. While risk and security personnel are often first on hand to gather details, expanded research into recent or recurring audit findings around related practices, policy adherence, timely remediation in response to similar, historically recent incidents can also add valuable context and content to the investigation’s findings and recommendations. Audit can also participate in performance of chain of custody processes employed by security professionals to secure material artifacts and assets supporting forensic work related to a cyber incident. The result of combined Audit, Security, and Cyber Risk efforts can lead to a more complete understanding of root causes, and lead to more precisely targeted and effective remediation activities.
Determining and Validating Risk Assessment
Integrate Audit input to validate risk assessment and remediation. Audit can provide specific vetted findings to validate or challenge assessment data, based upon controls discovery, incident, operational, policy adherence or 3rd party regulatory findings, and evaluation of project states (remediation activity). Through this participation, Audit can also help bridge the apparent gap between cyber and operational risk, as well as help leverage common controls with compliance obligations, including contractual ones with partners or other 3rd party suppliers. 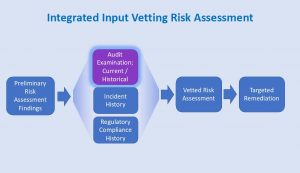 This can provide a quality check on risk assessment that enhances value and confidence by senior management, and by extending the input to content beyond technical cyber specifics, fosters a more comprehensive and inclusive view of risk across the enterprise. For example, an operating area reporting an assessment of low risk related to data management might be inclined to change its report when presented with recent audit findings of several incidents of lost or leaked data, and a general lack of understanding across staff of data categorization policies. Likewise, an audit of an operating area might take note that since patching of servers managing logistics schedules had become more up-to-date, there were fewer outages, resulting in operation efficiencies and savings, thus supporting reduced risk scores related to server patching practices. This is an example of a finding common to but upon initial inspection, un-apparently related events, between cyber risk and operations. This sort of collaborate cross discipline vetting of risk assessment provides a level of trust and value to a risk program that’s difficult to achieve otherwise. It fosters a platform for placing some common enterprise context to risk from many perspectives of a company’s activity. Such an enterprise approach encourages the creation and use of common terms (a taxonomy) to address risk, and helps line, staff, and executive management address risk with greater clarity and effectiveness regardless of their core competency or organizational perspective.
This can provide a quality check on risk assessment that enhances value and confidence by senior management, and by extending the input to content beyond technical cyber specifics, fosters a more comprehensive and inclusive view of risk across the enterprise. For example, an operating area reporting an assessment of low risk related to data management might be inclined to change its report when presented with recent audit findings of several incidents of lost or leaked data, and a general lack of understanding across staff of data categorization policies. Likewise, an audit of an operating area might take note that since patching of servers managing logistics schedules had become more up-to-date, there were fewer outages, resulting in operation efficiencies and savings, thus supporting reduced risk scores related to server patching practices. This is an example of a finding common to but upon initial inspection, un-apparently related events, between cyber risk and operations. This sort of collaborate cross discipline vetting of risk assessment provides a level of trust and value to a risk program that’s difficult to achieve otherwise. It fosters a platform for placing some common enterprise context to risk from many perspectives of a company’s activity. Such an enterprise approach encourages the creation and use of common terms (a taxonomy) to address risk, and helps line, staff, and executive management address risk with greater clarity and effectiveness regardless of their core competency or organizational perspective.
Cyber Security Compliance Audits
Integrate Audit into Cyber Risk and Security Process Evaluation. Like examinations of the practices in any other operating area of the enterprise, audits of cyber risk and security can and should examine the mechanics and underpinnings supporting these processes across its organizational scope. 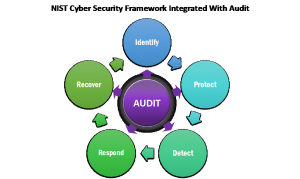 Reviewing cyber risk management policies, procedures, and the accuracy and completeness of documentation on hand is important. So too, is determining how internal governance works, ensuring that it leads to informed and effective decisions and directions effectively targeting reported findings. Scope and frequency of reviews should balance useful information needs with the potential invasiveness and operational disruption of the audit process. Staff education, including professional and technical skills presence to execute roles as presented in current job descriptions is an important but sometimes overlooked area for review. Audit can also explore how well stated controls frameworks are expressed through practices in the cyber risk and security programs, whether common controls with other business requirements are being considered, and how well resulting information is reported and published to and leveraged by internal stakeholders. Such an internal quality check on a cyber risk program provides strength and confidence in its presence and validity.
Reviewing cyber risk management policies, procedures, and the accuracy and completeness of documentation on hand is important. So too, is determining how internal governance works, ensuring that it leads to informed and effective decisions and directions effectively targeting reported findings. Scope and frequency of reviews should balance useful information needs with the potential invasiveness and operational disruption of the audit process. Staff education, including professional and technical skills presence to execute roles as presented in current job descriptions is an important but sometimes overlooked area for review. Audit can also explore how well stated controls frameworks are expressed through practices in the cyber risk and security programs, whether common controls with other business requirements are being considered, and how well resulting information is reported and published to and leveraged by internal stakeholders. Such an internal quality check on a cyber risk program provides strength and confidence in its presence and validity.
Tools for Collaboration
Leverage platform software to facilitate integration. Managing and facilitating the gathering, organization, storage, analysis, reporting and publication of cyber risk data along with integration of input from an audit function, and risk from operational, financial, legal, and other disciplines across a business enterprise can become complex. That’s why Integrated Risk Management (IRM) platforms were developed. They offer functions and features to model procedures into automated practices to simplify and standardize these operational necessities facing risk, audit, security, and other operating disciplines. They make data sharing across functions straightforward and offer a single authoritative and trusted source for risk, audit, incident, and related data that are secure and accessible to authorized staff working to service these disciplines. IRM software platforms offer the tools and features needed to efficiently realize the processes and benefits of collaboration and inclusion of Audit into the Cyber Risk Program described in this blog, as well as in Part One of the blog series.
About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.
DoubleCheck offers Cybersecurity Risk Management software that specifically addresses business needs and best practices. Please click here for more information.

