Subconsciously, we all manage risk throughout our daily lives. We pack an umbrella in case it rains, (unless we live in the Pacific Northwest where that’s considered unnecessary). We check our car tire pressure and fluid levels before a long road trip. We bring along water for a summer hike, and so on. You can think of many more. But when it comes to our business lives, we sometime find ourselves staring into a blank screen when it comes to taking the first step in structuring a risk management program. So, here’s a suggestion: begin by crafting a Risk Register. An easy statement to make, so let’s continue on and examine just how to go about making, refining, and maintaining one, and then how to use it as a building tool to get tangible value from your risk program.
Establish A Business Context
Often overlooked, this is a vital beginning step to assure business relevance and promote meaningful dialogue with company leadership. Examine the business basics of your company, specifically who you are and what you do. Answering the following types of questions can help you document those business basics:
- What are your core products and services?
- What are your key strategic objectives (i.e., capital accumulation, liquidity, reputational excellence, service leadership, etc.)?
- How does leadership and other stakeholders measure value (i.e., revenue, earnings, stock appreciation, sales volume leadership, brand recognition, to name a few)?
- How is this value created?
- What places strategic objectives, operating performance, and resulting value at risk?
- What is the scope of your risk program (enterprise, organizational unit, business segment, other)?
Once you’ve done this evaluation, examine the content. Pay particular attention to the terminology and language that works best to communicate these answers clearly. Take some time to vet your responses with others to assure they are clear, concise, and accurately reflect your company and its business. These should be terms you continually reference when describing, reporting, and discussing risk in all your communications. Words matter. Everyone needs to be on the same page with regard to risk.
Define Risk
There is art and craft to effectively doing this. If defined at too granular a level of specificity, it become unmanageable; and conversely, if done too broadly, the definition evaporates into meaningless messaging. This is where your business context becomes a helpful tool. One solid definition could be the “effect of uncertainty on the achievement of objectives.” You may also find it useful to look at each core objective and ask, “what events or situations might hinder or thwart the achievement of this objective?” You may think of other questions to help you explore risks. For instance, consider value chains. These are situations where one operational event or outcome may lead to a series of others that result in a negative impact upon a seemingly unrelated area. An example would be:
Scheduled maintenance updates to patch a group of data servers fall behind plan, leading to a short term outage in scheduling software and requiring manual operation. This, in turn, results in delayed and missed product deliveries contributing to a decline in product revenue for the period.
Generally, server maintenance isn’t viewed as an item that is clearly linked to revenue. But such linkage can occur and the circumstance cited is actually a reflection of one company’s past experience. Having stakeholders with a deep knowledge of your operations and their process integration can help reveal some of these risk situations. Understanding and identifying such relationships in value chains can also assist in the development of mitigation plans to help address either likelihood and/or severity (in this case, by completing patch updates to servers). In some disciplines, this kind of thinking is referred to as “systems thinking”.
Expressing risks in terms of their impact upon operational achievement of objectives is a way of establishing clear relevance to senior leadership, those individuals who are responsible for allocating resources to your program to help mitigate and manage identified risks, and sponsor remediation efforts to manage them. They are the key decision-makers who establish budgets and allocate resources.
 Once you’ve built your preliminary set of risks to objectives, you will then be in a position to enlist operational stakeholders as actual risk owners, individuals who are subject matter experts (SMEs) and who can add detail and specificity with respect to core disciplines. These should include, but not specifically be limited to, IT, Finance, Audit, Operations, Product Development, Support Services, Procurement, Third Party Management, Regulatory Compliance, and Facilities. Their input, aligned to your business practices and culture, will form the basics of your Risk Register. A crucial part of the risk survey process will be to ask what’s actually in place now to mitigate these risks. Keep those answers for consideration of controls, which you may map against regulatory or contractual obligations.
Once you’ve built your preliminary set of risks to objectives, you will then be in a position to enlist operational stakeholders as actual risk owners, individuals who are subject matter experts (SMEs) and who can add detail and specificity with respect to core disciplines. These should include, but not specifically be limited to, IT, Finance, Audit, Operations, Product Development, Support Services, Procurement, Third Party Management, Regulatory Compliance, and Facilities. Their input, aligned to your business practices and culture, will form the basics of your Risk Register. A crucial part of the risk survey process will be to ask what’s actually in place now to mitigate these risks. Keep those answers for consideration of controls, which you may map against regulatory or contractual obligations.
Process – Integrate The Register From the Bottom Upward
Make no mistake – your risk register is the foundational pillar for establishing an Enterprise Risk Management (ERM) program. It needs to be installed, embedded and thoroughly integrated throughout an organization in order to:
- Assure the active management of risks as a process
- Set priorities and actionable resource allocation to address risk
- Uncover and oversee the mitigation of the universe of risks
- Expose any hidden, value-adding opportunities
- Demonstrate itself as a usable, independent but integral regimen (not as a stand-alone, ivory-tower hypothesis), in order to maximize its contribution to the company’s mission
Very simply, consistent with the establishment of the risk register, the mission statement for an ERM program can be stated as
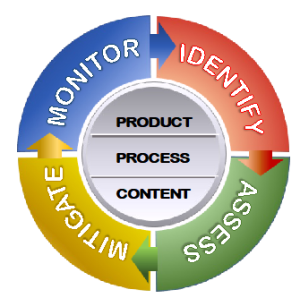
“…the process to identify, assess, mitigate and monitor all enterprise-wide risks that might impair the company’s ability to achieve its strategic business objectives.”
We’ve talked about the functions, processes and features of an ERM solution in many of our other blogs. A vital point: your ERM solution should clearly be understood as stand-alone and not a mere adjunct to other corporate functions, like compliance or internal audit. It is a discipline of its own and needs to be strategically designed and tactically executed, on an iterative (day-in-and-day-out) basis, using a risk register vehicle that is:
Going one step further, this Risk Register is not just a “nice to have” choice but rather a corporate initiative that is:
- Urgent – tomorrow is not soon enough
- Mandatory – avoids potential catastrophe and/or dereliction of duty
- Foundational – risk register “buckets” (causes, consequences, controls and key risk indicators) and metrics (severity, likelihood, and velocity) inform the components of ERM actionability – identification, assessment, mitigation and monitoring
- Collaborative – content provides operating managers and staff with a consistent framework and language to structure risk related actions and report accomplishments, issues, and recommendations.
- Connected – to the success of strategic objectives
- Value-oriented – satisfying myriad needs across a wide spectrum of stakeholders, such as:

Content – Applying Controls and Frameworks
Examining the all the attributes of the risks you’ve identified in your register allows you to accomplish two important tasks. First, you can readily see the reliance on, or the impact of, mitigation, for each risk. The sum total of mitigation serves to reduce inherent likelihood and severity to its current residual level. Secondly, you can use a framework to see if there are any significant gaps in your register you might want to address.
Process and Product – Enter The Risk Assessment
If there is only one activity to be used most often to define the core of ERM, the one aspect that is most readily identifiable and recognized, it’s the risk assessment! This is the action step that drives mitigation and helps prioritize monitoring. This is where your risk “health” is determined. If your risk register is a thermometer, this is where you take your company’s temperature. The register can critically evaluate which of the risks in your universe are appropriately addressed and where additional mitigation is most urgently needed. The findings of the assessment define your current state in the context of your business’ needs and goals, and drive your program’s response. The features of the tools you use to do this, through your GRC platform or whatever else you might use, are all focused upon a review of the content of the register, a determination of risk to your business by designated risk owners, with stated accountability. The information needs to be intentionally focused on a select few attributes (likelihood, severity, direction and velocity) and metrics need to be straightforward and clearly understood. Very importantly, you also need reporting tools to organize, analyze, and present the data into meaningful messages.
Product – Reporting
You’ve built your register, supplemented content, assessed your risk, and now you need to share what you’ve learned with decision makers and stakeholders. If you are working with a GRC tool where reporting is embedded within, where standard reporting, such as the generation of heat maps, counts and lists of most critical risks and such is generated right from your assessment data, that’s a strong beginning. If not, you want to generate visual and narrative statements of findings that answer some basic questions:
- What are our most significant risks?
- Which are most likely to have significant events occur?
- Where are they located?
- How are they prioritized, using enterprise-wide rating scales
- What is the current residual state (after controls) for each risk?
- What will it take, in terms of additional resources, to further mitigate them?
There are countless, additional questions that can be asked, based on the fulsome risk surveys received from subject matter experts. These further inquiries are healthy and will drive further conversation. Visualization is important to helping non-technical executives understand your assessment findings in business terms. It’s exactly why you built your register in the context of the business’ goals and mission. Further, you need a means of securing, publishing, and distributing this important information to key stakeholders, within control, in a secure manner. Risk assessment findings reports often contain highly confidential information, and you need the capability to manage publication and distribution carefully. Your Board of Directors, as well as your Executive Committee, are accountable for addressing and managing risk to their shareholders, regulators, customers, and other stakeholders. ERM is the discipline, and the risk register is the most valuable tool, that provides all of these varied stakeholders with the information and guidance to make quality decisions to manage and mitigate risk effectively
Product—Process—Content: The DoubleCheck Standard
While this, and many other blogs here, offer guidance on many risk management issues, they all point towards the benefit of utilizing a quality GRC tool to support execution. DoubleCheck understands that these three attributes of a GRC (Process, Product, and Content) are essential to delivering the critical services, tools, and capabilities companies require to tactically execute upon the four elements of day-to-day risk management (Identify, Assess, Mitigate, and Monitor) with efficiency and effectiveness. Further, services and features are highly integrated into one package. Reporting is embedded to rather than independently aligned to content and processes, making the risk management practice a seamless effort rather than a disjointed one. Whether out-of-the-box core functionality, or serving as a streamlined front-end to a larger enterprise (ERP) offering, or to an expansive, dedicated, tailored through configuration, custom fit to your company’s needs, DoubleCheck offers product, processes, and content designed to support all your enterprise risk management needs.
The next blog will expand upon the various use cases that can greatly benefit from a pre-populated, fully integrated ERM solution.

About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through the creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.

