Third Party Risk Management (TPRM) is more than just management of a group or category of business relationships. It is a program unto itself with its own unique characteristics and methods. Too often, TPRM is viewed and undertaken as a procurement process subset. That can lead to a collection of discrete transactions managed on a demand basis. This approach may lead to the impression of governance, but it misses the mark for understanding your program as a larger business process. So, let’s take a look at TPRM from this perspective and see what opportunities and insights may be revealed.
Evaluating Your Current State
In past blogs we’ve talked about specific vendors operating within a risk management process. Looking at third parties as a category of resources, a different understanding is needed. Imagine a heat map for your TPRM participating companies. How many partners would represent high risks? What does your risk distribution look like? Which suppliers provide critical services? Are there any for which you have no alternative due to their unique capabilities? Are any of those ranked as high risk cases? Ranking and arraying your third party resources will give you a clear snapshot of your third party risk position from a portfolio perspective. This snapshot gives you a clear picture 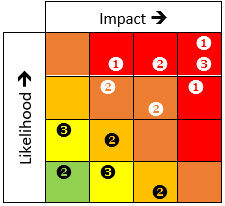 that’s useful to communicate a position, or the change in position of overall TPRM for business leaders concerned with business continuity, planning, and yes, procurement, of course. You can see that many, perhaps most in this case, are high ranking vendors that are also high risk. You could achieve this through a comprehensive listing as well, but I’ve found that the visual presentation of status or “state” data often leads to greater and faster communication and comprehension by recipients across all management levels and fields of expertise. You may find a combination of the two works equally well or even better within your own business culture.
that’s useful to communicate a position, or the change in position of overall TPRM for business leaders concerned with business continuity, planning, and yes, procurement, of course. You can see that many, perhaps most in this case, are high ranking vendors that are also high risk. You could achieve this through a comprehensive listing as well, but I’ve found that the visual presentation of status or “state” data often leads to greater and faster communication and comprehension by recipients across all management levels and fields of expertise. You may find a combination of the two works equally well or even better within your own business culture.
Evaluating Third Party Assessment Processing
Knowing the relative distribution of risk across your portfolio of third party providers is an important step. Exploring the details of their current participation in your risk process helps you evaluate where you are in addressing these risks. There’s a calendar (or should be) noting the schedule for initiating assessments for each of your providers. Some representing high risk for your business may be at least annual, or semi-annual, while low risk providers may be on less frequent schedules. Current contract provisions, or other regulatory obligations may reflect these requirements. Are your assessments beginning on time? Which, if any, have been deferred? For how long? Are the reasons documented? Does the revised timing violate agreements in force? Are there mitigating steps you need to take in the interim? Compare these answers to your risk distribution to see if you have significant issues where risk to your firm, or in the nature of your partner’s engagement with you, offer significant exposure. Also, check to see if your calendar has created seasonal high volume periods followed by gaps of minimal activity. Where possible, check to see if some start dates might be flexible and can help you balance out the distribution of work to reduce or avoid “peak assessment periods”.
Next, take a look at where providers are within the workflow of your assessment process. Take note of several factors, specifically process step, staffing for expert review of submissions, and apparent delays not addressed. Are there bottlenecks in your workflow? If there are, they may be due to dependence upon subject matter expert (SME) review where there are too few SME’s for the workload entering that part of the risk evaluation workflow. There’s a tendency to over-estimate the capacity of these experts to take on these tasks, particularly if these reviews are subordinate to other daily responsibilities. Just as the demand for SME review can require flexibility of scheduling, there also needs to be a capability to provide equally elastic capability to evaluate content from your providers in a timely fashion. Also, if you are using some of the automated workflow services a GRC platform often provides, review your workflow automation configurations and assignments. It’s often useful to establish escalation triggers that automatically advance assignments to alternate or higher level resources after a set period of inactivity. This alerts others to a delay in the workflow, and also point attention to a possible imbalance between SME service demand and capacity. Stepping back, look at the current state of all your assessments, to gain an understanding of where such imbalances might occur before they happen, taking the opportunity to manage your resources to the most effective use you can.
Contract Review
Not all third party risks are cyber in nature. One of the most challenging for some organizations is managing the portfolio of contract provisions resulting from all the different third party providers a firm may employ. There are a number of moving parts to track. Expiration dates, performance obligations, agreement and regulatory compliance obligations, triggers for discounts, interim payments, or any other terms that may be costly or lead to missed opportunities. Not every term or condition in a contract will tie to an annual event calendar. Some may be quarterly, semi-annual, or on other schedules unique to its terms. The risks surrounding contracts aren’t necessarily cyber in nature, but they may be financial and often can incorporate compliance matters. These can have a cascading impact upon other areas, and are equally important to a holistic approach to managing third party risk.
Where Are Your Vendors?
This isn’t a rhetorical question. Are they all located in close proximity to you geographically? If they are, then all your location based risks may have equal or more application to your suppliers and partners. Ideally some primary and secondary partners would be located outside your proximity so that weather or event-driven happenings would automatically compile third party outages with any of your own. One of the benefits of cloud offerings is the opportunity to disperse content across significant geographies to mitigate or prevent disruptions due to an event in one location. It’s important to review your portfolio of third parties and their geographies, both local and extended (if they have services spread across or among a wide geographic range) to identify any clusters of partners or providers set into one geography. If you do, note where. They may not be proximate to your locations, but may reside in places with a very different risk profile you’ll want to factor into the overall assessment of risks related to any specific vendor.
Frameworks, TPRM, and C-SCRM
Certainly, with regard to cyber risk and TPRM it worth a look at NIST’s Key Practices in Cyber Supply Chain Risk Management. Managing your vendors is a critical component of Cyber Supply Chain Risk Management, or C -SCRM. Having a comprehensive C-SCRM also means extending the scope of your TPRM practices to include:
- Engaging Key Suppliers in Resilience and Improvement Activities
- Assessment and Monitoring Throughout the Supplier’s Relationship
- Incorporating Third Parties in Plans for Full Life Cycle Review
- Where Appropriate, Assessing Suppliers’ Cyber capabilities
Using a framework such as NIST’s C-SCRM 8276 provides you with guidance on the range and scope of activities and practices to employ to build out a program to address and understand your cyber exposure across the full extent of your supply chain practices.
- If you are already applying the NIST Cyber Security Framework, these practices are largely represented within the details of the standard.
- Also, SP 800-161 Rev. 1, Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations (2nd Draft), offers more guidance.
This is essential to your overall risk management program at an enterprise level, and should encompass operational, financial and logistical as well as cyber risks and mitigation strategies. It’s likely you will impact internal policies, contract management, supplier procurement, on-boarding, and compliance along the way. Frameworks will also help you position your supply chain risk issues so it’s clear where the risk resides in processes in addition to suppliers or other actors. This is useful context for expressing cyber and other risk category issues, findings, and recommendations to leadership in a business rather than technical content. Frameworks are useful tools for bridging the distance between technical and business perspectives of your enterprise. They help you organize content and represent it in ways meaningful to senior leadership and other stakeholders.
GRC As A Holistic Platform
I often discuss how a governance, risk, and compliance software platform (GRC) can help address the issues discussed in an article. GRC platforms often afford the ability to aggregate data from many practices and processes to assemble a more complete picture of a subject area’s current risk state. Data from regulatory reviews, audits, risk assessments, incidents, project tracking, financial reports, and operating metrics, to highlight some, may all be incorporated into a GRC to create a more complete and comprehensive understanding of risk state and current dynamics withing a subject area of your organization. On an enterprise level, this data resource can be used to fuel a useful and realistic assessment of your supply chain practices, including key third party services and materials providers. Often, inclusion of content from areas such as Audit are restricted to specific controls compliance with respect to cyber activities or best practices. That’s a short sighted approach and a missed opportunity. Including content from reviews of bills of materials, or other procurement related supply chain process artifacts may reveal some surprising but important knowledge of critical vulnerabilities in your supply chain methods at a holistic view of risk for your enterprise. Likewise, data generated by operating performance metrics, or other data sources, aligned in the presence of data from these other areas may also yield new understanding and insight.
GRC’s may sometimes be like the well known detective’s magnifying glass, focusing upon and offering useful, but concealed insight, by careful inspection or alignment of seemingly incidental or unrelated data. Multiple data sources create context and alternative perspectives. The ability to gather and refocus data into information, through the use of a GRC’s analytical and data presentation tools, represents a clear advantage to your understanding of risk across your enterprise, and a fundamental, holistic awareness of risk for your TPRM practices, and supply chain overall.
About the Author:
Simon Goldstein is an accomplished senior executive blending both technology and business expertise to formulate, impact, and achieve corporate strategies. A retired senior manager of Accenture’s IT Security and Risk Management practice, he has achieved results through the creation of customer value, business growth, and collaboration. An experienced change agent with primary experience in financial, technology, and retail industries, he’s led efforts to achieve ISO2700x certification and HIPAA compliance, as well as held credentials of CRISC, CISM, CISA.
Some observations from DoubleCheck Software on Third Party Risk Management Platforms and Reporting
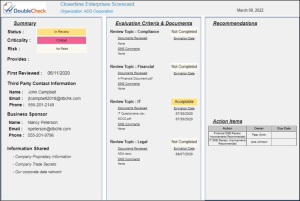
It is critical to have a holistic viewpoint on your Third Party Risk Management program. Sound, real-time reports and dashboards keep management informed at each step of the TPRM process. Reports 1 & 2 below are examples of TPRM reports generated from the DoubleCheck TPRM system. These reports are all part of an embedded Business Intelligence platform available in every DoubleCheck GRC module.
Report 1 (Third Party Status Report) demonstrates a collective view and status of all Third Party vendors. Report 2 (Third Party Scorecard) dives deeper into a specific vendor and details Contact Information, Evaluation Criteria and Documentation, Recommendations, and Action Items.
Third Party Status Report:

Third Party Scorecard:
Click for more on DoubleCheck’s Third Party Risk Management or Cyber Security Risk Management programs.

